Jointly analysing cyber security information without sharing
Jointly analysing cyber security information without sharing
 Friday 10 July 2020
Friday 10 July 2020 On July 7th, 2020, at a webinar organized for members of CIO Platform Nederland, TNO introdced an ongoing research project in the field of the exchange of cyber security information and Secure Multi-Party Computation (MPC). In this blog post, we'll make the information from the webinar more widely available, as MPC and cyber security can be an interesting and valuable combination for anyone who is working on cyber security (threat) information.
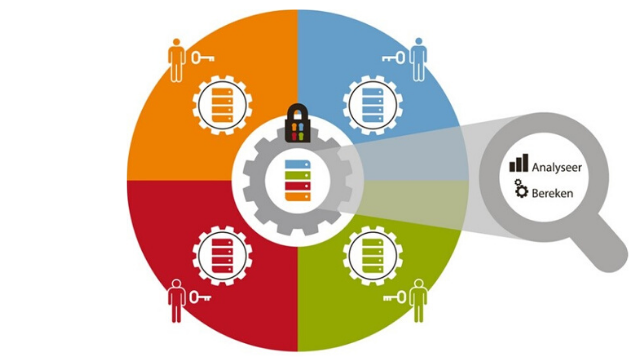
TNO is conducting exploratory research into Secure Mult-Party Computation (MPC) and cyber security information because it expects that valuable analyzes are possible when calculating confidential 'information security data' using MPC. The strength of this technology is that it makes analyzing sensitive data from multiple parties possible, without actually sharing this data.
Throughout 2020 TNO will be working together with other interested parties in order to gain experience with MPC and generate ideas and solutions. They have a lot of freedom to choose partners, test this technique in practice and to investigate its viability.
What is MPC?
Secure Multi-Party Computation (MPC) is a ‘toolbox’ of cryptographic techniques that allows several different parties to combine their (encrypted) data with (encrypted) data from other parties, with the aim of having previously agreed analyzes take place. The agreements are recorded in a mathematical protocol that can replace a trusted third party, and only in accordance with this protocol do analyzes take place on the data. Distinctive and of added value is the fact that the data itself is not exchanged.
Important features of the technique are: the data remains safe, data is not decrypted for the analyzes, it is not possible to deviate from (the number of) parties included in the protocol, the data from the parties cannot be traced, many calculations can take place and it can be integrated with existing tooling. The only thing that is shared is the outcome of the analyzes. Please watch the video about MPC. For more information and videos, please visit www.tno.nl/mpc.
Looking for use cases
The relevance of MPC has been proven in various economic sectors and domains. Application in the cybersecurity domain is relatively new, but could potentially make a major contribution to an information sharing paradox:
| Yes Information about how others are doing or what they are seeing is useful. |
Paradox
|
NO |
Due to the new character of the technique, identifying a use case is a challenge. Many companies have cyber security (threat) information at their disposal, but how does that compare with the information of others? Can we learn more when we compare data, or merge without knowing exactly what is being merged? Does MPC complement the informal relationship of trust? These questions form the starting position of the exploratory TNO research.
Does your company have any cyber security information that you would like to know from other companies, but which you are hesistant or unable to share yourself?
Do you want to know more? Please contact the project leader of this project Marie Beth van Egmond, marie_beth.vanegmond@tno.nl.
More news
Kick off session CxOs in the Maritime Sector | Data in the Port Ecosystem
 Friday 19 July 2024 Knowledge sharing on digitization topics relevant to the maritime sector. Meetings are organized by/in cooperation with CIO Platform Netherlands and are open to organizations wishing to share knowledge on substantive issues. CIO Platform Netherlands reserves the right to deny access to meetings. full story
Friday 19 July 2024 Knowledge sharing on digitization topics relevant to the maritime sector. Meetings are organized by/in cooperation with CIO Platform Netherlands and are open to organizations wishing to share knowledge on substantive issues. CIO Platform Netherlands reserves the right to deny access to meetings. full storyA quick look back at the first six months of 2024
 Friday 12 July 2024 A nice summer blog of our new board member Edward Cox, also General Manager Louwman Group Services. Have a nice summer! full story
Friday 12 July 2024 A nice summer blog of our new board member Edward Cox, also General Manager Louwman Group Services. Have a nice summer! full storyAnnual Day 2024 - Aftermovie
 Monday 08 July 2024 A record number of CIO Platform Nederland members gathered on June 6th to celebrate our community's valuable and sociable Annual Day together under the banner 'Elevate your Digital Transformation'. Watch the aftermovie here. full story
Monday 08 July 2024 A record number of CIO Platform Nederland members gathered on June 6th to celebrate our community's valuable and sociable Annual Day together under the banner 'Elevate your Digital Transformation'. Watch the aftermovie here. full storyResearch on labour market shortages, help us reach 100 and help yourself!
 Monday 24 June 2024 The shortage of qualified ICT talent is a brake on growth for many organisations. Together with other organisations, we are committed to tackling this challenge. We would like to ask for the help of our members by filling out a survey. full story
Monday 24 June 2024 The shortage of qualified ICT talent is a brake on growth for many organisations. Together with other organisations, we are committed to tackling this challenge. We would like to ask for the help of our members by filling out a survey. full story